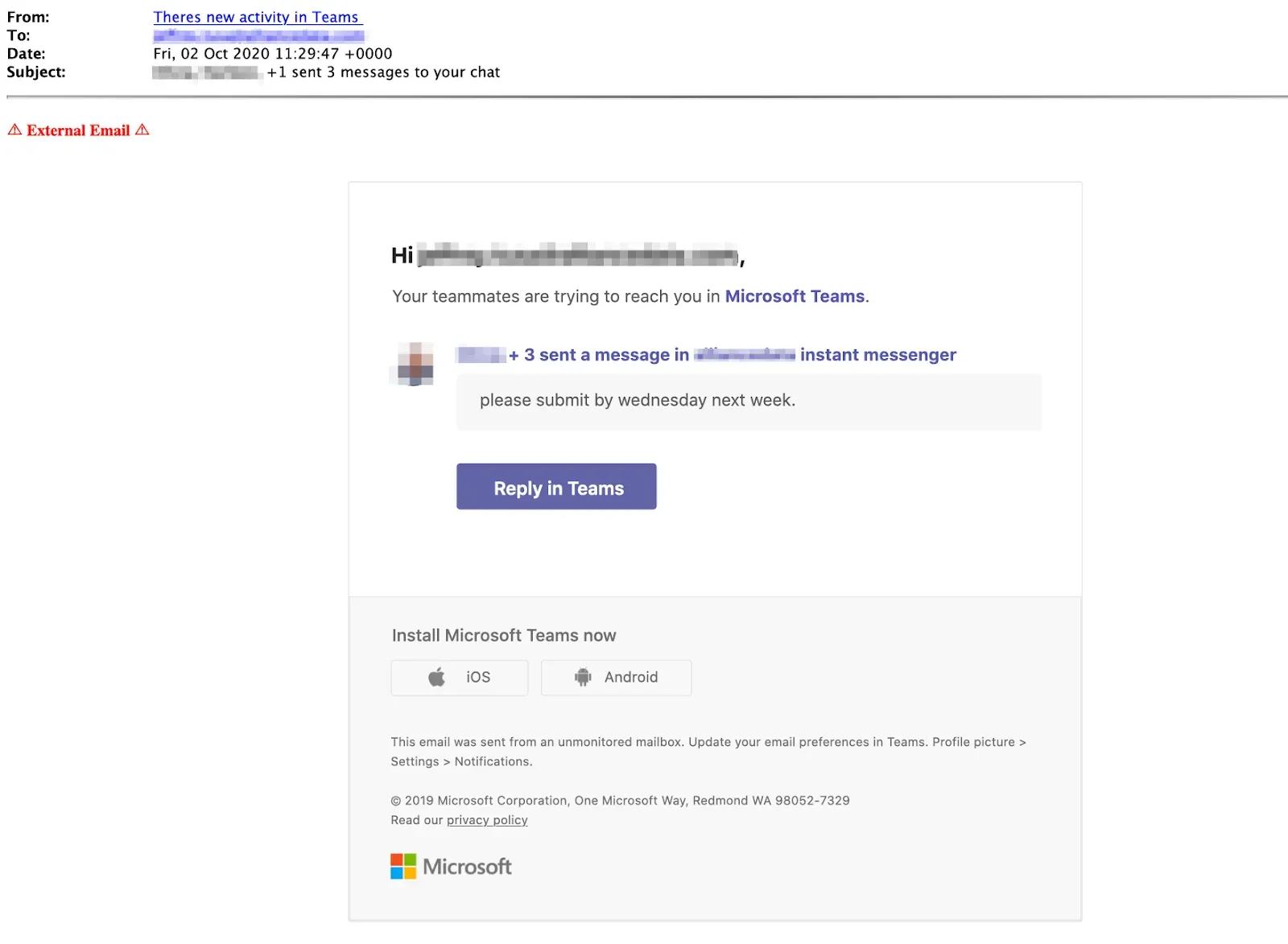
The Microsoft Teams phishing scam has emerged as a critical threat, particularly as digital criminals, possibly tied to Russian state interests, exploit the platform to trick users into surrendering their authentication tokens. These fraudulent invites pose a serious risk to sensitive information, allowing attackers to gain unauthorized access to emails and cloud data across various sectors, including government and healthcare. Microsoft has attributed this alarming trend to a group known as Storm-2372, which has been actively targeting organizations since August. As these Kremlin cyber threats escalate, it’s essential for users to remain vigilant and aware of the tactics employed by these malicious actors. By understanding the nuances of device code phishing and its implications, individuals can better protect themselves from the growing wave of Russian phishing attacks.
In recent months, a sophisticated cyber threat has surfaced that utilizes the Microsoft Teams platform as a conduit for phishing attempts. This alarming trend showcases how cybercriminals are leveraging trusted communication tools to launch deceptive attacks aimed at harvesting sensitive credentials. Often associated with Russian hacking groups, these phishing schemes are not just an isolated incident but part of a broader strategy involving various Kremlin cyber threats. The tactics employed, such as device code phishing, allow attackers to exploit users’ trust in legitimate communication channels, leading to significant security breaches. Understanding the landscape of these phishing threats, including those attributed to groups like Storm-2372, is crucial for enhancing Microsoft security and safeguarding personal and organizational data.
Understanding the Microsoft Teams Phishing Scam
The Microsoft Teams phishing scam has emerged as a significant threat, particularly targeting key sectors such as government, healthcare, and technology. Cybercriminals, potentially linked to the Kremlin, have adopted deceptive tactics to lure unsuspecting victims into providing sensitive information. This scam primarily revolves around fraudulent Microsoft Teams meeting invitations designed to appear legitimate, thus tricking users into disclosing their authentication tokens. By leveraging trusted platforms like Microsoft Teams, these attackers aim to bypass traditional security measures.
The ongoing campaign, attributed to a group identified as Storm-2372, has been active since August and showcases the evolving nature of Russian phishing attacks. The attackers employ a strategy known as device code phishing, where they manipulate victims into entering their credentials on a fake login page. This technique not only highlights the sophistication of the attackers but also underscores the urgent need for heightened security awareness among users. As the lines between authentic communications and cyber threats blur, recognizing the signs of phishing becomes paramount.
The Role of Storm-2372 in Cybercrime
Storm-2372 is a notorious group known for its cyber espionage activities that align with Russian state interests. This group has been linked to various phishing scams, including those that exploit platforms like Microsoft Teams. Their operations are characterized by a calculated approach, often involving the establishment of trust with potential victims through messaging apps before launching their phishing attacks. By impersonating trusted contacts, they increase the likelihood of success in their malicious endeavors.
The group’s tactics extend beyond mere phishing; they utilize sophisticated methods to extract sensitive information from their targets. Reports indicate that Storm-2372 employs Microsoft Graph to sift through users’ emails for critical credentials. This level of intrusion poses a severe threat not only to individuals but also to organizations, as compromised accounts can lead to widespread data breaches and loss of sensitive information. Understanding the modus operandi of Storm-2372 is crucial for developing effective countermeasures against such cyber threats.
Device Code Phishing Explained
Device code phishing is a cunning method used by cybercriminals to gain unauthorized access to user accounts. In this attack vector, the perpetrators trick victims into entering a verification code on what appears to be a legitimate Microsoft login page. Once the victim inputs this code, the attackers receive a valid access token, enabling them to infiltrate the victim’s accounts without needing their actual passwords. This method is particularly dangerous because it exploits trust in well-known services like Microsoft.
The implications of device code phishing are severe, especially for organizations that rely on Microsoft services. Attackers can easily move laterally within a compromised network, sending phishing messages to other users using the victim’s email account. This can lead to a domino effect of breaches, further endangering the organization’s data integrity. As such, understanding device code phishing is essential for developing robust defenses against these sophisticated cyber threats.
The Impact of Kremlin Cyber Threats
Kremlin cyber threats have significantly evolved, with groups like Storm-2372 leading the charge in sophisticated phishing attacks. These threats not only compromise individual security but also pose risks to national security and critical infrastructure. By targeting key sectors such as energy, healthcare, and government, these cybercriminals aim to undermine public trust and exploit sensitive information for political or economic gain.
The geopolitical implications of such cyber threats cannot be overstated. As tensions rise, the likelihood of state-sponsored cyberattacks increases. Understanding the motivations behind these attacks is crucial for organizations to bolster their defenses. By recognizing the patterns of Kremlin cyber threats, businesses can implement more effective security protocols and training programs, reducing their vulnerability to future attacks.
Strategies to Combat Microsoft Teams Phishing Attacks
To mitigate the risks associated with Microsoft Teams phishing attacks, organizations must adopt a multi-faceted approach to cybersecurity. First and foremost, educating employees about the signs of phishing scams is vital. Regular training sessions can help staff recognize suspicious emails and messages, especially those containing urgent requests for authentication.
Additionally, implementing technical safeguards such as multi-factor authentication (MFA) can significantly reduce the chances of unauthorized access. Organizations are encouraged to enable conditional access policies that require users to re-authenticate under certain circumstances, further protecting sensitive information from cybercriminals. By combining user education with robust security measures, businesses can create a formidable defense against Microsoft Teams phishing scams.
The Evolution of Phishing Techniques
Phishing techniques have evolved dramatically over the years, becoming increasingly sophisticated and difficult to detect. Cybercriminals have shifted from generic emails to targeted attacks that leverage social engineering tactics, making them more convincing. The rise of device code phishing exemplifies this evolution, as attackers manipulate victims into providing access tokens through seemingly legitimate channels like Microsoft Teams.
As phishing tactics continue to advance, it is crucial for organizations to stay ahead of the curve. Regularly updating security protocols, conducting vulnerability assessments, and fostering a culture of cybersecurity awareness can help organizations defend against these evolving threats. By understanding the latest trends in phishing techniques, businesses can better prepare themselves to counteract these malicious strategies effectively.
Recognizing Signs of Phishing Emails
Identifying phishing emails is critical for preventing successful attacks. Common signs include unsolicited messages that create a sense of urgency or fear, asking the recipient to click on links or provide sensitive information. Phishing emails often contain poor grammar, misspellings, or suspicious sender addresses, which can serve as red flags for users.
In the case of Microsoft Teams phishing scams, recipients may receive invites that look official but lead to fraudulent login pages. Users should always verify the authenticity of unexpected invitations, especially those requesting sensitive information. By being vigilant and educated about these signs, individuals can significantly reduce their risk of falling victim to phishing schemes.
The Importance of Cybersecurity Awareness
Cybersecurity awareness is paramount in today’s digital landscape, especially given the rise in sophisticated phishing attacks. A well-informed workforce is the first line of defense against cyber threats. Regular training sessions, workshops, and simulated phishing exercises can empower employees to recognize and respond to potential threats effectively.
Organizations must foster a culture of cybersecurity, encouraging open communication about potential threats and breaches. By prioritizing cybersecurity awareness, businesses can reduce their vulnerability to attacks like the Microsoft Teams phishing scam, ultimately safeguarding their sensitive data and maintaining trust among clients and stakeholders.
Microsoft’s Role in Combatting Cyber Threats
As a leading technology provider, Microsoft plays a crucial role in combating phishing threats, including those targeting Microsoft Teams. The company continually monitors for suspicious activities and provides updates on known threats. Microsoft’s proactive approach includes educating users about emerging phishing techniques and offering tools to enhance security, such as multi-factor authentication and conditional access policies.
Moreover, Microsoft collaborates with law enforcement agencies and cybersecurity experts to track and mitigate the activities of groups like Storm-2372. By sharing threat intelligence and best practices, Microsoft aims to create a safer online environment for all users. Their ongoing commitment to cybersecurity is vital in the fight against the sophisticated tactics employed by cybercriminals.
Frequently Asked Questions
What is the Microsoft Teams phishing scam linked to Storm-2372?
The Microsoft Teams phishing scam identified as Storm-2372 involves fraudulent meeting invites sent by cybercriminals possibly affiliated with the Kremlin. This group targets individuals in key sectors, aiming to obtain authentication tokens that grant access to sensitive information like emails and cloud data.
How does device code phishing work in the context of Microsoft Teams phishing scams?
Device code phishing in Microsoft Teams scams involves attackers tricking victims into entering a device verification code on a legitimate Microsoft login page. Once the victim authenticates with this code, the attackers gain access tokens to the victim’s accounts without needing passwords or multi-factor authentication.
What measures can I take to protect against Microsoft Teams phishing scams?
To protect against Microsoft Teams phishing scams, only enable device code flow when necessary, and be vigilant about unsolicited meeting invites. If you suspect a phishing attempt, revoke any refresh tokens and consider implementing a conditional access policy for re-authentication.
What sectors are most targeted by the Microsoft Teams phishing scam linked to Russian hackers?
The Microsoft Teams phishing scam linked to Storm-2372 has primarily targeted government entities, NGOs, IT services, telecommunications, healthcare, higher education, and energy sectors across Europe, North America, Africa, and the Middle East.
What should I do if I receive a suspicious Microsoft Teams invite?
If you receive a suspicious Microsoft Teams invite, do not click on any links or enter any information. Verify the sender’s identity through other means, and report the incident to your IT department or cybersecurity team.
Why are Russian phishing attacks like Storm-2372 a concern for Microsoft Teams users?
Russian phishing attacks like Storm-2372 are a concern for Microsoft Teams users because they employ sophisticated tactics to deceive individuals into surrendering sensitive credentials, potentially leading to significant data breaches and unauthorized access to critical systems.
How does Microsoft respond to threats from Storm-2372 and similar groups?
Microsoft actively monitors for threats like Storm-2372 and informs affected customers. They also provide updates on the evolving tactics used by these groups and recommend security measures to protect users from phishing scams.
What has Microsoft discovered about the tactics used by Storm-2372 in Microsoft Teams phishing scams?
Microsoft has discovered that Storm-2372 builds rapport with victims via messaging apps and sends spoofed Microsoft Teams invites. They then utilize device code phishing to trick victims into providing access tokens, allowing unauthorized access to accounts.
| Key Point | Details |
|---|---|
| Phishing Method | Storm-2372 uses device code phishing to deceive victims. |
| Targeted Sectors | Government, NGOs, IT, telecom, health, education, energy sectors. |
| Attack Cycle | Attackers build rapport through messaging apps, then send spoofed Teams invites. |
| Access Method | Victims enter device verification codes on a legitimate Microsoft login page. |
| Data Harvesting | Attackers use valid access tokens to infiltrate user accounts. |
| Preventive Measures | Enable device code flow only when necessary, revoke tokens if phishing is suspected. |
Summary
The Microsoft Teams phishing scam is a sophisticated cyber threat where digital thieves, allegedly linked to the Kremlin, exploit Teams meeting invites to trick individuals into revealing their authentication tokens. This scam has targeted various sectors globally since August, employing tactics that involve building trust through messaging platforms before sending fraudulent invites. To safeguard against such threats, it is critical to limit device code usage and stay vigilant against phishing attempts.