Buffer overflow vulnerabilities are a critical issue in the realm of cybersecurity, often described by US authorities as “unforgivable defects”. These vulnerabilities emerge when software attempts to write more data to a memory buffer than it can handle, leading to potential exploitation by malicious actors. The Cybersecurity and Infrastructure Security Agency (CISA) and the FBI have highlighted the importance of secure coding practices to mitigate such software vulnerabilities, urging developers to adopt memory-safe programming languages. By learning how to exploit buffer overflow scenarios, attackers can hijack software functionality or crash systems, making it essential for developers to address these memory safety flaws proactively. Addressing these vulnerabilities is not just a technical necessity; it is a critical component of safeguarding national and economic security, as emphasized in the recent CISA FBI joint advisory.
Buffer overflow vulnerabilities, also known as memory corruption bugs, present significant challenges in software development and cybersecurity. These flaws occur when programs exceed their allocated memory space, potentially leading to unauthorized access or system crashes. With the increased reliance on technology, it is vital for developers to understand how these issues arise and implement secure coding practices to prevent them. The FBI and CISA have highlighted the dire need for adopting memory-safe languages as a proactive measure against these prevalent software vulnerabilities. In light of these concerns, it is evident that enhancing memory safety is crucial for maintaining the integrity of software systems.
Understanding Buffer Overflow Vulnerabilities
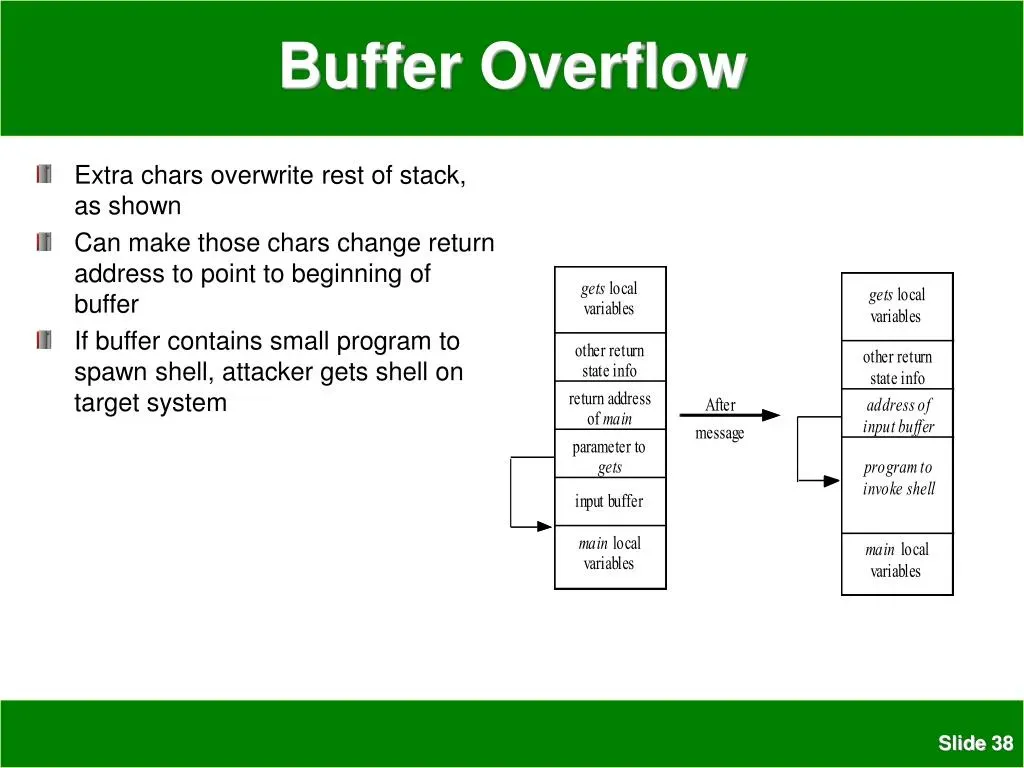
Buffer overflow vulnerabilities are critical flaws that can lead to severe security breaches in software systems. These vulnerabilities occur when a program writes more data to a block of memory, or buffer, than it can hold. This excess data can overflow into adjacent memory spaces, corrupting or altering the execution of other processes. As detailed by US authorities, such vulnerabilities are categorized as ‘unforgivable defects’ primarily due to their preventability through the adoption of secure coding practices.
The exploitation of buffer overflow vulnerabilities can facilitate a range of malicious activities, from unauthorized data access to complete system takeover. Attackers can craft specific inputs that manipulate the software’s memory allocation, allowing them to hijack program execution or crash the application. It is crucial for developers to understand these risks and implement robust coding practices, as the consequences of such security flaws can compromise not only individual systems but also broader network infrastructures.
The Role of Secure Coding Practices in Preventing Vulnerabilities
Adopting secure coding practices is essential for developers aiming to mitigate software vulnerabilities, especially those related to memory safety. By integrating principles of secure-by-design into their development processes, programmers can reduce the risk of introducing flaws such as buffer overflows. This involves using languages that inherently prevent memory safety issues, like Rust or Go, and avoiding outdated programming languages like C and C++, which are prone to such vulnerabilities.
Moreover, organizations must prioritize training their developers in secure coding techniques and the use of modern tools that help in identifying potential vulnerabilities early in the software development lifecycle. Implementing static analysis, unit tests, and utilizing tools like AddressSanitizer can significantly enhance the security posture of applications. By fostering a culture of security awareness, companies can better protect their systems from the exploitation of buffer overflow vulnerabilities and similar threats.
CISA and FBI’s Advisory on Memory Safety Flaws
The recent advisory issued by the Cybersecurity and Infrastructure Security Agency (CISA) and the FBI emphasizes the urgent need for developers to address memory safety flaws. Highlighting the existence of six notable buffer overflow vulnerabilities, the agencies underscored the importance of transitioning away from unsafe programming practices. The advisory categorized these flaws as not only technical issues but also significant threats to national security, urging immediate action to remediate them.
In their joint alert, CISA and the FBI provided insight into specific vulnerabilities that have been exploited in the wild. For instance, CVE-2025-0282, a critical stack-based buffer overflow in Ivanti’s Connect Secure, was identified as a zero-day vulnerability, showcasing the immediate threat posed by memory safety flaws. The agencies recommend that developers adopt memory-safe languages and utilize advanced development tools to combat these vulnerabilities head-on.
Transitioning to Memory-Safe Programming Languages
Transitioning to memory-safe programming languages such as Rust, Go, and Swift is a proactive approach to mitigating software vulnerabilities, particularly buffer overflow flaws. The adoption of these languages can significantly reduce the risk of memory safety issues, providing developers with built-in safeguards against common errors that lead to security breaches. While the shift from traditional languages may require considerable effort, the long-term benefits of enhanced security and stability are undeniable.
For organizations looking to make this transition, a phased approach is recommended. This involves gradually converting existing codebases while simultaneously implementing mitigation technologies to address vulnerabilities in legacy systems. As emphasized by CISA and the FBI, such measures will not only improve the resilience of software products but also lower the likelihood of future exploits that could compromise national and economic security.
Compiler Flags and Tools for Enhanced Security
Utilizing compiler flags that enforce compile-time and runtime protections is a vital strategy for bolstering the security of software applications. These flags can help developers catch potential memory safety issues before they manifest as vulnerabilities in production environments. By enabling such protections, programmers can mitigate the risks associated with memory overflow and other related defects, ensuring that their code adheres to modern security standards.
In addition to compiler flags, employing advanced tools like AddressSanitizer and MemorySanitizer can provide developers with insights during the testing phase. These tools perform real-time checks for memory safety issues, allowing for the early detection of vulnerabilities before they can be exploited. Incorporating these practices into the development lifecycle is essential for creating secure software that withstands the evolving landscape of cyber threats.
Conducting Aggressive Adversarial Testing
Conducting aggressive adversarial product testing is crucial for identifying and mitigating buffer overflow vulnerabilities in software. This approach entails employing methods such as static analysis, fuzzing, and manual reviews throughout the development process. By simulating attack scenarios, developers can uncover weaknesses in their applications and address them proactively, rather than reactively responding to security incidents after they occur.
Furthermore, performing root-cause analysis of past vulnerabilities allows organizations to learn from previous mistakes and strengthen their security protocols. This continuous improvement cycle fosters a more resilient software development environment, where security is a priority rather than an afterthought. As emphasized by US authorities, the proactive identification and remediation of vulnerabilities is essential for safeguarding software against exploitation.
The Importance of Memory Safety in Software Development
Memory safety is a critical aspect of software development that directly impacts the overall security of applications. Flaws associated with memory management, such as buffer overflows, present significant challenges for developers, as they can lead to unauthorized access and system crashes. By prioritizing memory safety, organizations can reduce the likelihood of these vulnerabilities and enhance the reliability of their software products.
To achieve memory safety, developers should adopt modern programming practices and tools that facilitate safe memory management. This includes using memory-safe languages, implementing rigorous testing protocols, and conducting thorough code reviews. By fostering a culture of memory safety within development teams, organizations can not only protect their products but also build user trust and confidence in their software solutions.
Learning from Past Vulnerabilities
Understanding and learning from past vulnerabilities is essential for improving software security practices. Developers must analyze historical data on buffer overflow vulnerabilities to identify common patterns and mistakes that led to exploits. By examining case studies and advisories, such as those issued by CISA and the FBI, developers can gain valuable insights into how to mitigate similar risks in their own projects.
Moreover, conducting thorough post-mortem analyses of vulnerabilities can help organizations refine their development processes and better prepare for future threats. This proactive approach to learning ensures that teams remain vigilant and responsive to emerging vulnerabilities, ultimately leading to more secure software products that withstand the test of time.
The Future of Software Security
The future of software security heavily relies on the ability of developers to adapt to evolving threats and implement cutting-edge practices. As buffer overflow vulnerabilities continue to pose significant risks, the emphasis on memory safety will likely grow stronger. Organizations must invest in training their development teams on the latest secure coding practices and tools to stay ahead of potential exploits.
Additionally, collaboration between government agencies and the private sector will be vital in addressing software vulnerabilities. By sharing information, best practices, and resources, developers can create a more secure software ecosystem. As the landscape of cybersecurity continues to shift, a collective effort will be essential in combating the persistent threat of buffer overflow vulnerabilities and other software defects.
Frequently Asked Questions
What are buffer overflow vulnerabilities and why are they significant?
Buffer overflow vulnerabilities are software flaws that occur when a program writes more data to a memory buffer than it can hold. This overflow can overwrite adjacent memory, leading to unpredictable behavior, crashes, or even allowing attackers to gain unauthorized access. They are significant because they are common weaknesses in software security that can be exploited by malicious users to execute arbitrary code, making them a critical concern for developers and organizations.
How can secure coding practices help prevent buffer overflow vulnerabilities?
Adopting secure coding practices is essential in preventing buffer overflow vulnerabilities. Developers should prioritize using memory-safe programming languages like Rust, Go, and Swift, which inherently reduce the risk of memory safety flaws compared to languages like C and C++. Additionally, implementing techniques such as input validation, proper buffer management, and regular code reviews can significantly mitigate the chances of introducing these vulnerabilities.
What was the recent CISA and FBI advisory on buffer overflow vulnerabilities?
The recent advisory from the Cybersecurity and Infrastructure Security Agency (CISA) and the FBI classified buffer overflow vulnerabilities as ‘unforgivable defects.’ The agencies emphasized the urgent need for developers to abandon unsafe coding practices that lead to these memory safety flaws. They highlighted specific vulnerabilities, such as CVE-2025-21333 and CVE-2024-49138, which had severe implications for national and economic security.
What are some common examples of buffer overflow vulnerabilities?
Common examples of buffer overflow vulnerabilities include CVE-2025-0282, a stack-based buffer overflow in Ivanti’s Connect Secure, and CVE-2024-38812, a heap overflow in VMware vCenter. These vulnerabilities have been exploited by attackers, often before patches were released, underscoring the critical need for secure coding practices in software development.
Why should developers stop using C and C++ due to buffer overflow vulnerabilities?
Developers are urged to stop using C and C++ because these languages are prone to memory safety flaws, such as buffer overflows, due to their lack of built-in protections. The CISA and FBI recommend transitioning to memory-safe programming languages like Rust, which help to prevent these vulnerabilities and enhance overall software security.
What strategies can organizations implement to address existing buffer overflow vulnerabilities?
Organizations can address existing buffer overflow vulnerabilities by implementing a phased transition to memory-safe languages, utilizing compiler flags that enforce safety checks, and conducting aggressive product testing. Techniques such as static analysis, fuzzing, and employing tools like AddressSanitizer can help identify and mitigate memory safety issues in legacy code.
How do buffer overflow vulnerabilities affect national security?
Buffer overflow vulnerabilities pose a significant risk to national security, as they can be exploited by attackers to gain unauthorized access to critical systems. The CISA and FBI have indicated that these vulnerabilities can lead to severe consequences, including data breaches and system compromises, which may impact both economic stability and national defense.
What is the importance of conducting adversarial product testing for buffer overflow vulnerabilities?
Conducting adversarial product testing is crucial for identifying buffer overflow vulnerabilities. This testing should include techniques like static analysis, fuzzing, and manual code reviews throughout the development lifecycle. By actively seeking out potential weaknesses, developers can strengthen their software against exploit attempts and ensure better overall security.
| Key Point | Description |
|---|---|
| Definition of Buffer Overflow Vulnerabilities | Buffer overflow vulnerabilities occur when software writes more data to memory than allocated, causing excess data to spill into other areas. |
| Impact of Buffer Overflow Vulnerabilities | These vulnerabilities can be exploited by attackers to hijack program flow or crash applications, posing significant security risks. |
| Government Advisory | The FBI and CISA classified these vulnerabilities as ‘unforgivable defects’ and urged developers to adopt secure coding practices. |
| Examples of Vulnerabilities | Six identified vulnerabilities include critical bugs in Microsoft, VMware, and Citrix products that have been exploited before patches were released. |
| Recommended Practices | Developers are encouraged to use memory-safe languages like Rust, Go, and Swift, and to implement phased transition plans away from C and C++. |
| Testing and Analysis | Conduct aggressive adversarial product testing and utilize tools like AddressSanitizer for memory safety checks. |
Summary
Buffer overflow vulnerabilities represent a critical security concern in software development, as highlighted by US authorities. They emphasize the need for developers to adopt secure coding practices to prevent such vulnerabilities, which can lead to significant risks, including unauthorized access and system crashes. By transitioning to memory-safe programming languages and employing rigorous testing methods, developers can significantly reduce the occurrence of these vulnerabilities and enhance overall software security.