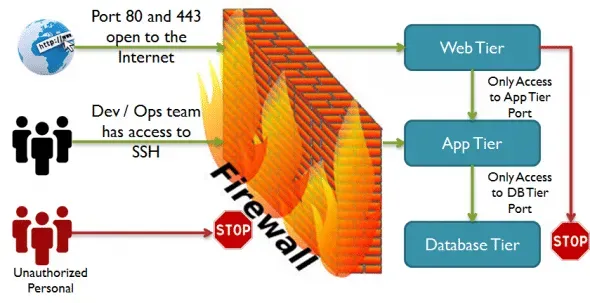
A Linux firewall is essential for protecting your system from unauthorized access and various cyber threats. With the right firewall configuration in Linux, you can effectively manage the flow of network traffic, ensuring that only legitimate connections are allowed. Tools like iptables and firewalld provide robust solutions for implementing security measures tailored to your networking needs. Additionally, the Uncomplicated Firewall (UFW) simplifies the management of firewall rules, making it easier for users to enhance their network security. This comprehensive guide will walk you through the process of setting up a Linux firewall, ensuring that your system remains shielded against potential intrusions and attacks.
Firewalls serve as critical defenses in network security, and understanding their role is pivotal for any Linux user. By leveraging various firewall management tools, such as iptables and firewalld, you can create a secure environment for your systems. Alternative methods like UFW also enable users to configure their firewalls simply and effectively. These tools help in filtering traffic and enforcing security policies, thus playing a vital role in defending against unauthorized access and cyber threats. In this guide, we will delve into the different types of Linux firewalls and provide practical steps for configuring them to ensure your network remains safe and secure.
Understanding the Importance of a Linux Firewall
A Linux firewall is an essential component of any system’s security infrastructure. It acts as a gatekeeper, controlling the flow of data between your machine and external networks. By setting up a firewall, you can effectively manage traffic, allowing only authorized communications while blocking potentially harmful connections. This proactive approach is vital in today’s digital landscape, where cyber threats are increasingly sophisticated.
Incorporating a Linux firewall into your network security strategy helps protect sensitive data and maintain the integrity of your system. By defining rules and policies, you can mitigate risks associated with unauthorized access, data breaches, and malware attacks. Understanding the significance of a robust firewall setup prepares you to confront these challenges head-on.
Frequently Asked Questions
What is the significance of a Linux firewall in network security?
A Linux firewall is crucial for network security as it safeguards systems against unauthorized access and cyber threats. By configuring specific firewall rules, it effectively manages the traffic entering and exiting the system, acting as a protective barrier between trusted internal networks and untrusted external connections.
How do I set up firewall configuration in Linux using iptables?
To set up firewall configuration in Linux using iptables, begin by reviewing the current rules with `sudo iptables -L`. Reset existing rules using `sudo iptables -F`, modify default chain policies with `sudo iptables -P <Chain_Name> <Action>`, and then add specific rules to accept or drop traffic. Finally, save your configuration to ensure it persists after a reboot.
What are the advantages of using firewalld for Linux firewall management?
Firewalld offers a dynamic and user-friendly approach for managing firewall rules in Linux. It allows for the assignment of network interfaces to zones, making it easier to configure and manage rules based on the network context. This flexibility helps ensure that the correct security policies are applied efficiently.
Can you provide an iptables tutorial for beginners?
An iptables tutorial for beginners should start with understanding its basic structure, which involves chains of rules determining the handling of network traffic. Begin by listing current rules with `sudo iptables -L`, resetting rules with `sudo iptables -F`, and then add ACCEPT or DROP rules to control traffic based on IP addresses and port numbers. Always remember to save your configuration.
What is UFW Linux and how can it simplify firewall management?
UFW (Uncomplicated Firewall) in Linux simplifies firewall management by providing a user-friendly interface for iptables. It allows users to easily enable the firewall, allow essential services, and block unwanted traffic using straightforward commands. This makes it ideal for users who may not be familiar with complex command-line operations.
How can I troubleshoot common firewall errors in Linux?
To troubleshoot common firewall errors in Linux, check for transient rules by ensuring all changes are saved, avoid excessive blocking by reviewing DROP rules, and verify zone configurations in firewalld to prevent unexpected traffic issues. Additionally, assessing logs can provide insights into blocked traffic and help refine your rules.
What are the best practices for maintaining a Linux firewall?
Best practices for maintaining a Linux firewall include regularly reviewing and updating firewall rules, implementing logging for monitoring traffic, thoroughly testing changes before deployment, and automating configurations with tools like Ansible to ensure consistency and reduce manual errors.
What tools are available for managing Linux firewalls?
Several tools are available for managing Linux firewalls, including iptables for robust command-line control, firewalld for dynamic management using zones, UFW for a simplified interface, and CSF (ConfigServer Security & Firewall) for comprehensive security solutions that include firewall functionalities.
How can I enable UFW on my Linux system?
To enable UFW on your Linux system, simply run the command `sudo ufw enable`. After enabling, you can configure it by allowing or denying specific services, such as allowing SSH with `sudo ufw allow ssh`, and check the status with `sudo ufw status` to ensure your rules are applied.
What is the role of connection states in a Linux firewall?
Connection states in a Linux firewall play a crucial role in determining how packets are handled. They indicate whether a packet is part of an existing connection or a new request. Utilizing connection states allows the firewall to apply more granular rules, enhancing security by allowing return traffic for established connections while blocking unsolicited requests.
| Key Points | Details |
|---|---|
| Importance of Linux Firewall | Crucial for safeguarding systems against unauthorized access and cyber threats. |
| Firewall Functionality | Manages incoming and outgoing traffic based on established rules. |
| Common Tools | Tools include iptables, firewalld, and nftables. |
| Types of Firewalls | Includes software and hardware firewalls, each with unique features. |
| Setting Up Firewalls | Can be configured using iptables, firewalld, or UFW. |
| Common Errors | Transient rules and excessive blocking can lead to issues. |
| Management Tips | Monitor regularly, save configurations, and test rules. |
Summary
A Linux firewall is an essential component for ensuring the security of your system. By effectively managing network traffic and utilizing tools like iptables and firewalld, you can protect against unauthorized access and cyber threats. This guide has outlined the various types of firewalls, their functionalities, and practical steps to configure them, emphasizing the importance of regular monitoring and updates to maintain a secure environment.